Radio frequency (RF and RFID) tags
by Chris Woodford. Last updated: January 3, 2022.
How many times have you walked through a store's doors and—to your extreme embarrassment—set off the anti-theft alarm? It's surprisingly easy to do, even when you've paid for your item and had it "deactivated" at the checkout. Anti-shoplifting alarms use a technology called RF (radio-frequency), while a similar (but more advanced) technology called RFID (radio-frequency identification) has many other uses, from tracking pets and public library stocktaking to collecting fares from bus passengers. Let's take a closer look at this cunning technology and find out how it works!
Photo: A typical RF security gate in a shop doorway in Birmingham, England. There's another one of these on the other side of the door. Sometimes these scanners are disguised so you can't see them, but more often they're designed to act as a very visible deterrent to shoplifters.
Sponsored links
Contents
RF tags use wireless technology
Radio or wireless is a way of transmitting energy through empty space—that is, instead of using a wire cable. The energy is carried by invisible waves of electricity and magnetism that vibrate through the air at the speed of light. The basic science and the practical technology of wireless communication was developed in the second half of the 19th century. During the early 20th century, "radio" came to mean audio programs beamed through the air from giant transmitters to cumbersome electronic boxes sitting in people's homes. When inventors found a way of sending pictures, as well as audio, television was born. Today, all kinds of things work using the same wireless technology, from digital radio and television to cellphones (mobile phones), and wireless Internet.
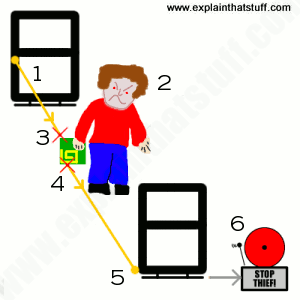
Radio and television involve sending radio waves in one direction only: from the transmitter at the radio or TV station to the receiver (the radio or TV set) in your home. Wireless Internet and cellphones are more sophisticated because they involve two-way communication. Your cellphone, for example, contains both a radio receiver (to pick up an incoming signal from the person you're speaking to) and a radio transmitter (to send your voice back to the other person). Radar is another technology that uses radio waves. Planes and ships fitted with radar transmitters send out beams of radio waves and listen for echoes—reflected radio beams bouncing back off other planes and ships nearby. Anti-shoplifting devices are a little bit like radar: they beam radio waves out into a store in the hope of catching a stolen book or CD as it passes by. But how exactly do they work?

Photo: An example of the kind of RFID tag used in book labels. It helps with automated stock control and (in some systems) might double-up as an anti-theft device. You can often see these by holding library paperbacks up to the light. This tag is a UPM Raflatac RaceTrack that can hold up to 1 kilobyte (1024 characters) of information. It operates at a relatively high radio wave frequency of 13.56 megahertz.
How RF works
Imagine your mission is to design an anti-shoplifting device using some old radio sets you found in the garage. You could build something a bit like a radar (with a combined radio transmitter and receiver), sit it by the shop doorway, and point it at people passing by. Radio waves would pass out from your transmitter, bounce off people walking past, and then reflect back to your radio receiver. The trouble is, this wouldn't actually tell you anything useful, because everyone would reflect the radio waves in exactly the same way! You wouldn't know whether people were shoplifting or not, because there would be no way to distinguish shoplifters from ordinary customers or people who hadn't bought anything at all. What you'd really need would be for shoplifters to reflect radio waves in a different way to everyone else. But how?

Photo: Look closely at this price and size label from a pair of shoes and you'll see it says "RFID" on the bottom. Peel it off, turn it over, and you'll find the tell-tale antenna pattern on the back.
Anti-shoplifting devices have cracked this problem. As well as having a transmitter and receiver at the doorway, every item in the store contains a concealed RF "tag". In bookstores and libraries, you'll find very discreet "soft tags," stuck to one of the inside pages. In record stores, the plastic shrink-wrap may have an RF tag stuck onto it, or CDs may be locked into large plastic cases with RF tags built into them, which can be removed only be a special tool at the checkout. In clothes stores, there is typically a "hard tag" (a chunky, round, white plastic tag) bolted onto each item with a sharp metal spike (sometimes the tag has ink inside it so it spills all over you and spoils the item you're trying to steal if you attempt to remove it). Some of these tags are cleverly concealed so you can't spot them. Others are deliberately very obvious and easy to see—so they deter you from stealing. The gates on the doorway (and the frequent alarms) are another very visible deterrent to shoplifters.
If you walk through the doorway without paying for something, the radio waves from the transmitter (hidden in on one of the door gates) are picked up by the coiled metal antenna in the label. This generates a tiny electrical current that makes the label transmit a new radio signal of its own at a very specific frequency. The receiver (hidden in the other door gate) picks up the radio signal that the tag transmits and sounds the alarm. Why doesn't the alarm sound when you pay for something? You may have noticed that the checkout assistant passes your item over or through a deactivating device (sometimes it's incorporated into the ordinary barcode scanning mechanism, and sometimes it's completely separate). This destroys or deactivates the electronic components in the RF label so they no longer pick up or transmit a signal when you walk through the gates—and the alarm does not sound.
What's the difference between RF and RFID tags?
It's all a bit more complex than I've made it sound so far because there are, in fact, two quite different types of RF tags and they work in a slightly different way. Often the term "RFID" is loosely used to describe both, but there's a big difference between them: RF tags all send the same, simple signal and simply tell the receiver that something is present; RFID tags send more complex signals that uniquely identify whatever they're attached to.
RF tags
These are the simplest RF tags and they're used mainly in what's called electronic article surveillance (EAS)—the anti-shoplifting technique I've described above. All the tags are exactly the same and none of them identify the articles to which they're attached. So in a store, RF tags set off the alarm when you try to steal something, but the alarm mechanism doesn't know what you're stealing, only that you're stealing something: there's no way of telling any one item from any another.
One of the most popular RF technologies is called acousto-magnetic (AM). A pulsed beam of radio waves from the transmitter strikes the tag, making it give off a precise frequency radio signal. The receiver picks up the signal, verifies that it's at the correct frequency, and then sets off the alarm. One big advantage of AM tags is that they can be scanned at quite a distance and at speed, making them popular in antitheft systems (which have only seconds to pick up a signal from someone walking or running through a shop doorway).
RF tags are sometimes known as transponders or chipless RFID tags.
RFID tags
These are more advanced and differ from simple RF tags in that they uniquely identify the article to which they've been attached: the radio signal that zaps from the article to the receiver contains a digitally encoded identifier. That's how self-checkout machines in libraries work: they beam radio waves into the RFID tag in the back of the book, receive the radio signal back from the book, and decode this to figure out a digital code that uniquely identifies which book you want to check out. A computer attached to the scanner does the rest (so in a library, the self-checkout machine communicates with the library's computer to update the main database whenever you check out or return a book). Unlike RF tags, RFID tags tend to work over much shorter distances. Some actually have to be held right next to a reader device, while others operate at a distance of 10cm (4 inches) or less.
Simple RFID tags are described as passive. Instead of containing batteries, they work entirely by responding to the incoming radio waves from the scanner or transmitter. There is just enough energy in those radio waves to activate the RFID chip. Passive tags typically send and receive signals only a few centimeters, but not much more. An alternative form of RFID technology, known as active tags, contain more advanced chips and tiny batteries to power them. They can send and receive signals over much greater distances.

Photo: Passive RFID: You can see the metal tracks of the antenna in this RFID tag quite clearly. This is the sort of tag used in library self-checkout systems.
Passive RFID tags contain just three components:
- The antenna—catches incoming radio waves and sends them back out again.
- The chip—generates a unique identifier code for the particular tag.
- The substrate—the backing material (typically paper or plastic) to which the antenna and chip are fixed.
As you can see from this photo, most of the space in an RFID tag is occupied by the antenna: the oval-shaped tracks around the edge. The antenna needs to be this big both to pick up radio waves from the transmitter and (because there are no batteries) to convert them into energy to power the chip. The chip itself is tiny—sometimes as small as the point of a pencil. Anti-shoplifting RF tags are often smaller and simpler than this: instead of needing a chip to generate a unique identifier code, all they have to do is receive the incoming radio waves and retransmit the same electromagnetic energy at a different frequency.